In today’s rapidly evolving digital landscape, ensuring the security of sensitive information and maintaining strict control over who has access to it is paramount. This is where Identity and Access Management (IAM) solutions come into play. Businesses need reliable IAM systems to safeguard their data, protect against cyber threats, and ensure compliance with regulations. SafeBix.com is a leading player in the field, offering a suite of IAM services and boasting certified resources to cater to your organization’s unique needs.
Understanding the Significance of IAM
Identity and Access Management (IAM) refers to the policies, processes, and technologies that enable organizations to manage and control access to their critical digital assets. It encompasses user authentication, authorization, and management of identities throughout their lifecycle. The main objectives of IAM are to enhance security, streamline user access, improve compliance, and reduce operational overhead.
SafeBix.com’s Comprehensive IAM Services
SafeBix.com understands that no two organizations are the same, which is why they offer a range of tailored IAM services to meet the diverse needs of businesses across various industries:
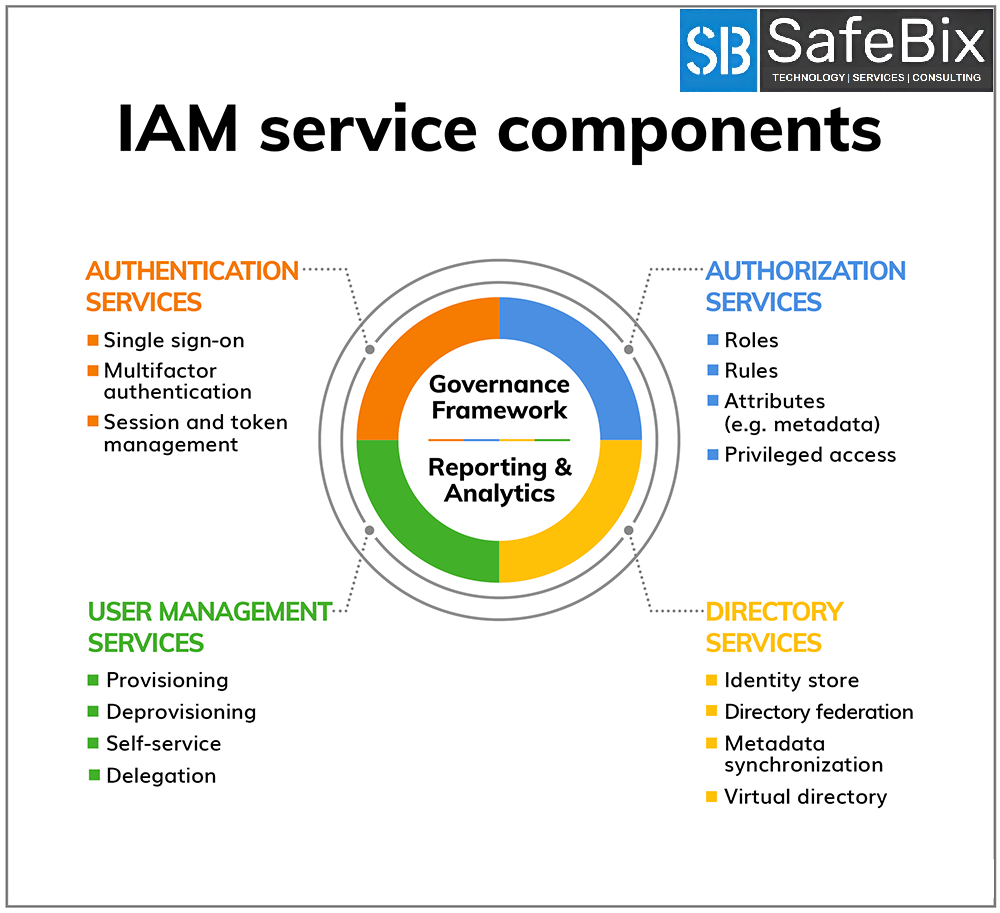
Identity Lifecycle Management: SafeBix.com assists organizations in creating, maintaining, and terminating user identities efficiently. They ensure that user access aligns with business roles and responsibilities, reducing the risk of unauthorized access.
Access Control: SafeBix.com helps you establish fine-grained access control policies. Their solutions enable organizations to grant or restrict access to specific resources based on user attributes and roles, thereby preventing unauthorized access.
Single Sign-On (SSO): Simplify user authentication with SSO solutions from SafeBix.com. Users can access multiple applications and services with a single set of credentials, enhancing user convenience while maintaining security.
Multi-Factor Authentication (MFA): Strengthen authentication processes with MFA solutions from SafeBix.com. By requiring multiple forms of verification, such as something you know (password), something you have (token), or something you are (biometrics), MFA significantly reduces the risk of unauthorized access.
Identity Governance and Administration (IGA): SafeBix.com’s IGA solutions help organizations maintain a centralized view of user access rights and privileges. This ensures that access remains in compliance with regulatory requirements.
Audit and Compliance: SafeBix.com provides robust auditing and reporting tools to help organizations monitor user activities, detect anomalies, and demonstrate compliance with industry regulations like GDPR, HIPAA, and more.
Certified Resources for IAM
SafeBix.com’s commitment to excellence is reflected in their team of certified IAM experts. Their professionals have undergone rigorous training and obtained industry-recognized certifications in IAM technologies and best practices. This ensures that when you partner with SafeBix.com, you’re working with experts who are well-versed in the latest IAM trends and technologies.
Having certified resources at your disposal means that SafeBix.com can offer expert guidance in designing, implementing, and maintaining IAM solutions that align with your organization’s specific needs. Whether you’re a small business or a large enterprise, their certified experts have the knowledge and experience to secure your digital ecosystem effectively.
Conclusion
In a world where data breaches and cyberattacks are on the rise, investing in robust Identity and Access Management solutions is not just good practice; it’s essential for safeguarding your organization’s sensitive information and maintaining trust with your stakeholders. SafeBix.com stands out as a trusted partner in this endeavor, offering a comprehensive suite of IAM services and certified resources to guide you through the complex landscape of identity and access management. With SafeBix.com by your side, you can rest assured that your digital assets are secure, compliant, and efficiently managed.
